
 Share
Share

 Print
Print
Security Explorer
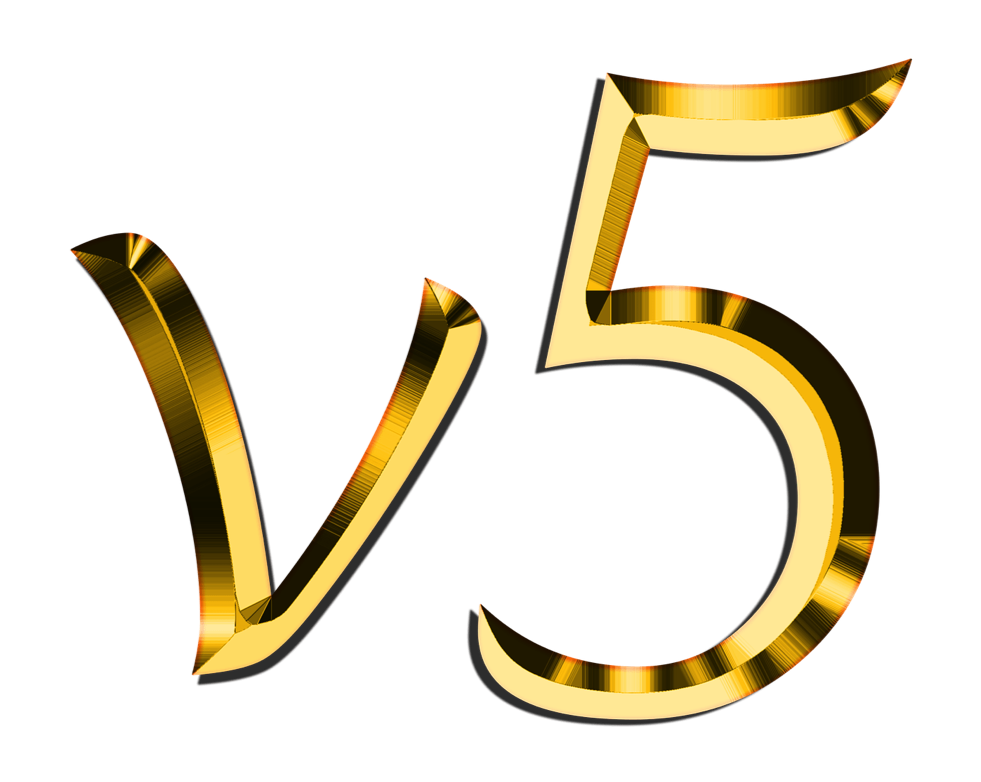
The Security Explorer is used by eMRO administrators to restrict or grant system access to their users. To reach the window go to System Administration / Explorer / Security Explorer. When new users are created, security limitations are among the first priorities administrators will apply. The Security Explorer allows users to be set up with the specific functionalities required for them to carry out their daily tasks. Access to various windows, tabs, buttons, and Wall passwords as well as sign-on functionalities are applied from this window.
Note: In Version 5 the Security Explorer has been redesigned while providing the same functionality.
To apply the necessary security levels, users must first understand the Log On process. For information regarding the different Log On methods refer to the System Administration topic Logging Into eMRO.
When opened, the Security Explorer is displayed as follows:

The functionality found in the Security Explorer can be applied through various methods. Security access can be applied by individual user or security for a specific window can be applied to groups of people at a time; the same is true for Wall Password setup. The Security Explorer has multiple features/layouts for creating and designating security controls.
Because similar functions can be applied through different methods, all of the functionalities and information available in the Security Explorer can be broken down as follows:
- Security Explorer Icons - Highlights the informational icons seen throughout the Security Explorer.
- Updating/Creating User Profiles - Specifies how User and Group Profiles are created and managed.
- Applying Security Access - Includes all different methods for applying security controls to users and/or groups.
- Applying Wall Passwords - Includes all different methods for applying Wall Password controls for users.
- Miscellaneous Admin Features - Lists extra options administrators have for controlling current system access.

 Share
Share

 Print
Print